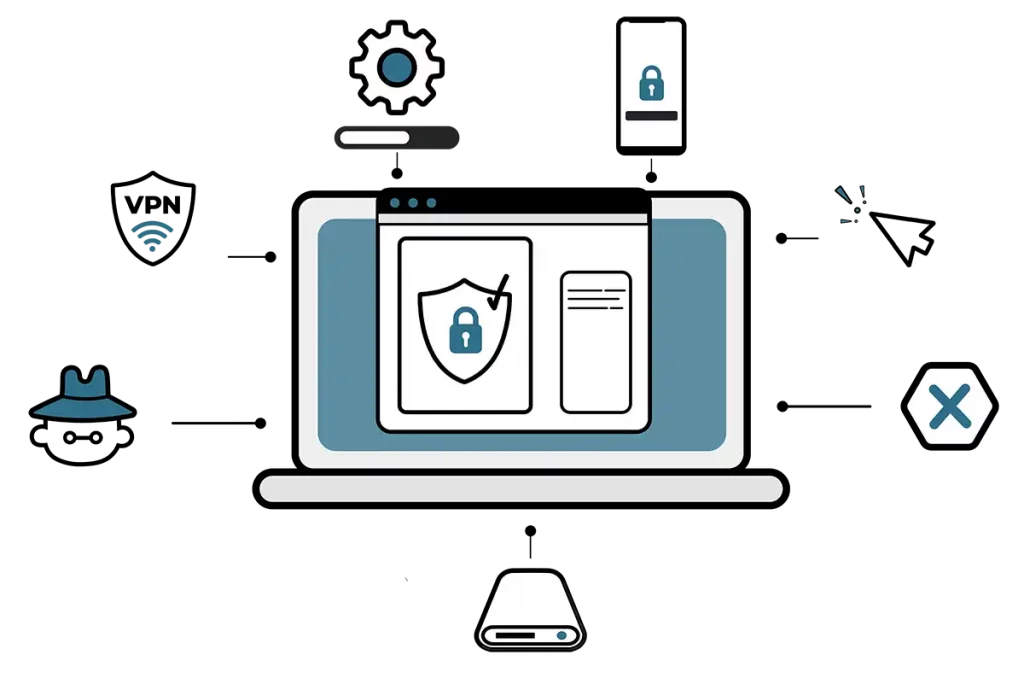
Protect your data with encryption
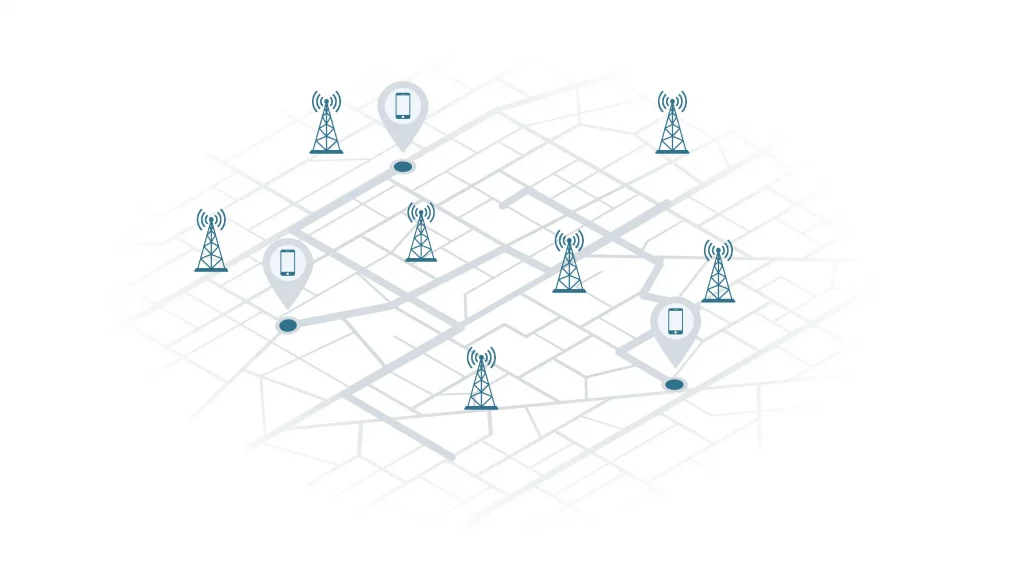
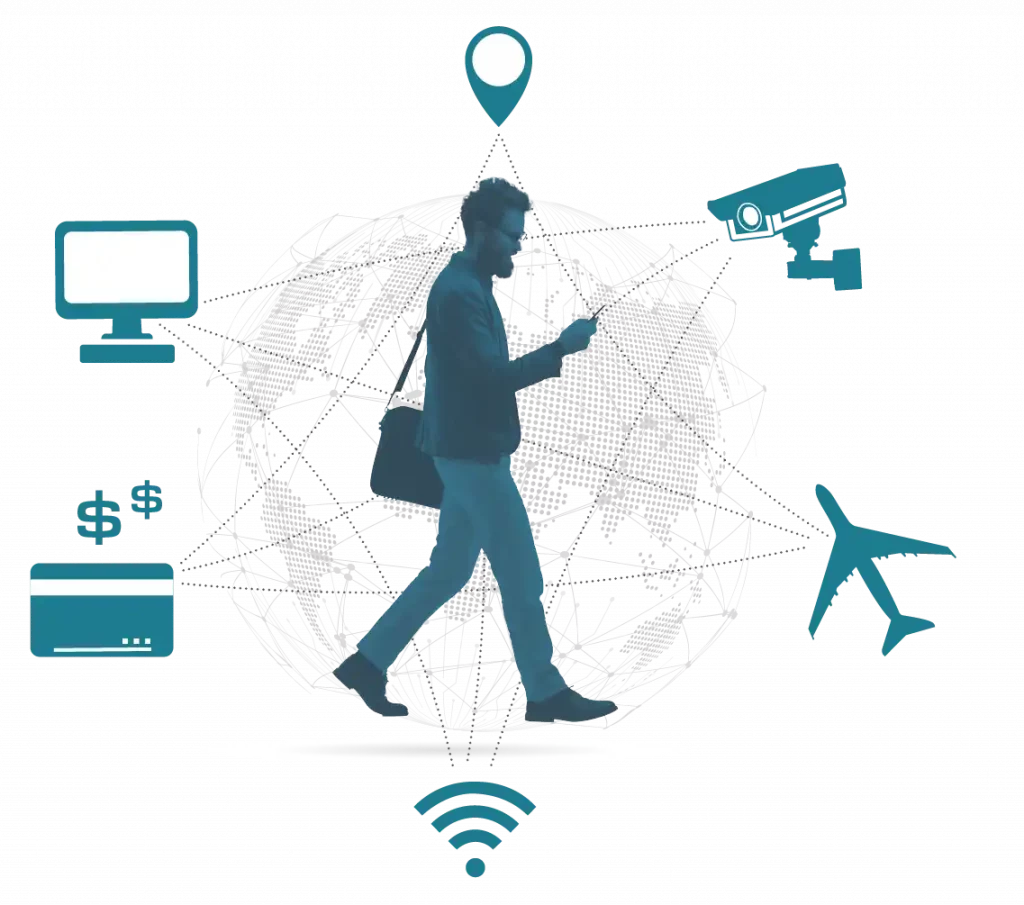
This week’s announcement by the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) about a massive cyberattack on telecommunications companies such as Verizon and AT&T, makes it clear: encryption is key to keeping communications secure. Understanding Encryption Encryption is an important component of digital privacy that allows you to keep your data secure. It …